Let’s Encrypt
Let’s Encrypt is a free, automated, and open certificate authority (CA). It simplifies digital certificates management, providing tools to automatize certificates release, renewal and revocation.
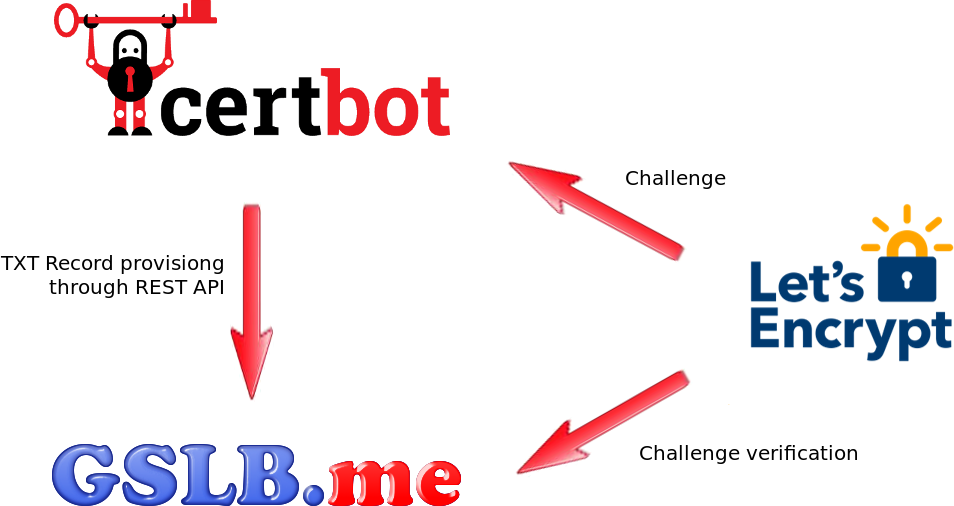
Let’s Encrypt supports several methods to make sure that an account key holder is the entity that is requesting certificates for a specific FQDN. One of such methods is known as DNS challenge.
GSLB.me can be used as your fully integrated DNS solution to provide letsencrypt with DNS challenges, so that your certificates are automatically released and managed.
The certbot script can be used to simplify the whole process.
Certbot official documentation is available here:
https://certbot.eff.org/docs/using.html#hooks
To use certbot and GSLB.me together you need to use the two scripts provided here below. The only configuration required is setting up the GSLBME_API_USERNAME and GSLBME_API_PASSWORD as your GSLB.me username and API password respectively.
dns-authenticator.sh:
#!/bin/bash # # GSLB.me - https://www.gslb.me # Letsencrypt DNS challenge authenticator # # Use your GSLB.me username and API password here GSLBME_API_USERNAME="your-gslb.me-username" GSLBME_API_PASSWORD="your-gslb.me-api-password" # Gets the top domain DOMAIN=$(expr match "$CERTBOT_DOMAIN" '.*\.\(.*\..*\)') DOMAINWITHNOTLD=$(echo $CERTBOT_DOMAIN | sed "s/$DOMAIN//g" | sed 's/\.$//') # Create the TXT challenge record CREATE_OUTPUT=`curl -s -u $GSLBME_API_USERNAME:$GSLBME_API_PASSWORD -X POST -H "Accept: application/json" -H "Content-Length: 0" -k https://api.gslb.me/record/$DOMAIN/_acme-challenge.$DOMAINWITHNOTLD/TXT/$CERTBOT_VALIDATION/120` RECORD_ID=`echo $CREATE_OUTPUT | python -c "import sys,json;print(json.load(sys.stdin)['id'])"` # Save info for cleanup echo $RECORD_ID > /tmp/CERTBOT_GSLB.me_$CERTBOT_DOMAIN # Commits the zone to make the newly created record active curl -s -u $GSLBME_API_USERNAME:$GSLBME_API_PASSWORD -X POST -H "Accept: application/json" -H "Content-Length: 0" -k https://api.gslb.me/commit/zone/$DOMAIN > /dev/null # Sleep to make sure the change has propagated sleep 5
dns-cleanup.sh:
#!/bin/bash # # GSLB.me - https://www.gslb.me # Letsencrypt DNS challenge cleanup # # Use your GSLB.me username and API password here GSLBME_API_USERNAME="your-gslb.me-username" GSLBME_API_PASSWORD="your-gslb.me-api-password" # Gets the top domain DOMAIN=$(expr match "$CERTBOT_DOMAIN" '.*\.\(.*\..*\)') if [ -f /tmp/CERTBOT_GSLB.me_$CERTBOT_DOMAIN ]; then RECORD_ID=$(cat /tmp/CERTBOT_GSLB.me_$CERTBOT_DOMAIN) rm -f /tmp/CERTBOT_GSLB.me_$CERTBOT_DOMAIN fi # Remove the challenge TXT record from the zone curl -s -u $GSLBME_API_USERNAME:$GSLBME_API_PASSWORD -X DELETE -H "Accept: application/json" -k https://api.gslb.me/record/$DOMAIN/$RECORD_ID > /dev/null # Commits the zone to make the newly created record active curl -s -u $GSLBME_API_USERNAME:$GSLBME_API_PASSWORD -X POST -H "Accept: application/json" -H "Content-Length: 0" -k https://api.gslb.me/commit/zone/$DOMAIN > /dev/null
A sample commandline to use in order to run certbot is:
certbot certonly --manual --preferred-challenges=dns --manual-auth-hook ./dns-authenticator.sh --manual-cleanup-hook ./dns-cleanup.sh -d fqdn.to.create.cert.for
This will tell certbot to run the dns-authenticator.sh script to automatically create the TXT record holding the letsencrypt challenge, and to run the dns-cleanup.sh script to remove the TXT record after the certificate has been released by letsencrypt.
To discover more about how to configure, use and integrate GSLB.me, you can browse our howtos.
